The US Cybersecurity and Infrastructure Security (CIS) agency on Thursday added two flaws to its catalog of known vulnerabilities, citing evidence of active exploitation.
These two high-severity issues are related to weaknesses in Zimbra’s communication mechanism, both of which can be chained to achieve unauthenticated remote code execution on vulnerable email servers.
CVE-2022-27925: (CVSS score: 7.2)
- Remote code execution (RCE) via mboximport from authenticated user (fixed in 8.8.15 patch 31 and 9.0.0 patch 24 released in March).
CVE-2022-37042:
- Bypassing authentication in MailboxImportServlet in versions 8.8.15 patch 33 and 9.0.0 patch 26, which was released in August, was fixed.
- If you are running an older version of Zimbra version (8.8.15) patch (33) or Zimbra version (9.0.0) patch 26, you should update to the latest patch as soon as possible.
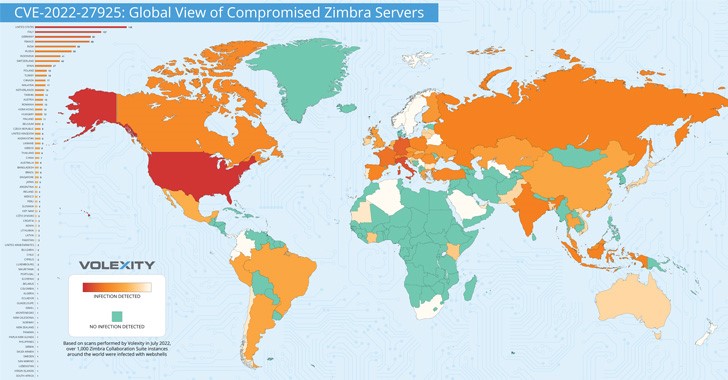
In short, the attacks involve exploiting the authentication bypass flaw to achieve remote code execution on the main server by uploading arbitrary files.
Also, more than 1,000 cases have been identified around the world that have been compromised using this type of attack, some of which are related to government departments and ministries, military branches, and companies with billions of dollars in revenue. to be