A recently discovered Linux-based ransomware known as Cheerscrypt has been released as the handiwork of a Chinese cyber-espionage group known for executing short-lived ransomware schemes.
Emperor Dragonfly uses open source tools written by Chinese developers for Chinese users, the company said in a report shared with The Hacker News. This confirms the claim that the users of Emperor Dragonfly ransomware are located in China.
The use of Cheerscrypt is the latest addition to a long list of ransomware families already used by the group in just over a year, including LockFile, Atom Silo, Rook, Night Sky, Pandora, and LockBit 2.0.
In its profile of the group, Secureworks added: “It is possible that Bronze Starlight is using ransomware as a smokescreen rather than financial gain, with the main motive being to steal intellectual property or perform espionage.”
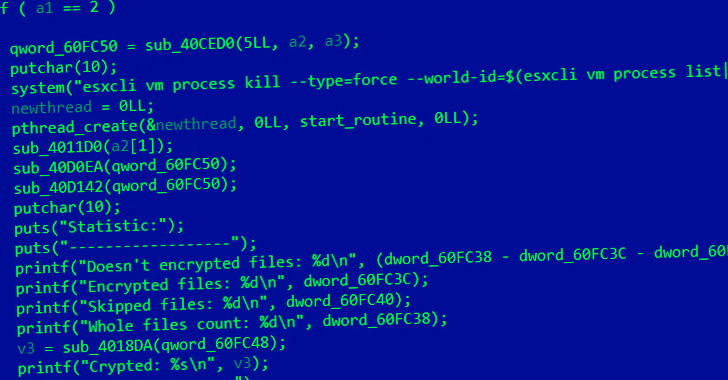
Cheerscrypt was first reported by Trend Micro in May 2022 and is known for its ability to target VMware ESXi servers as part of a tried-and-tested tactic called double extortion to force its victims to pay a ransom or risk exposing their data. did
It was also claimed that the act was in support of Ukraine, which displayed the message “Pride for Ukraine” on their dark web website.
Interestingly, this malware overlaps with the Linux version of the Babuk malware, whose reference codes were leaked in September 2021, and which is also the basis of Emperor Dragonfly’s Rook, Night Sky, and Pandora families.
The threat actor’s method of operation is further distinguished by managing all stages of the ransomware attack lifecycle, from initial access to ransomware deployment, without relying on affiliates and access brokers. Microsoft described DEV-0401 as a “lone wolf” actor.
The infection chains observed to date have used a critical Log4Shell vulnerability in the Apache Log4j library to compromise VMware Horizon servers to drop a PowerShell payload capable of delivering an encrypted Cobalt Strike beacon.